You are here
Map of State Responses in Lebanon
Publication Date: 2018
- The map is continuously updated.
- Each mapped state response is based on a typology devised by Lebanon Support.
- The objective of the map is to explore state responses by providing accurate data and relevant information on security operations happening on the territory.
Information sources: Media reports, NGO reports, aid actors reports, as well as first-hand data collected by the Lebanon Support team.
Date of start of data collection: May 15th, 2018.
- To get the most out of our map, make sure to read the map legend, and our typology below.
- To view a state response that took place in a specific location, first, find the location on the map by clicking on the relevant cluster. Then, you can click on the individual marker to explore the state response.
- If more than one state response took place in the exact same location, you can click on the individual marker, and use the arrows and numbers at the bottom of the pop up box to explore the various state responses mapped in this location.
- Our filters above can help you find state responses by location, acting body, method, objective, type of response, date, and more. At least one filter must be used for a search.


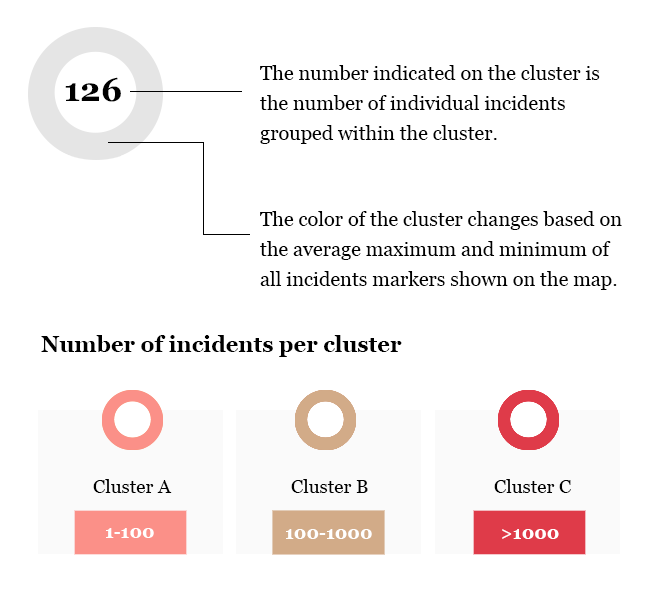
A cluster is a grouping of state response markers. Cluster marker colors indicate the number of state response grouped within that cluster.
Clustering works by dividing the map into a square grid and grouping the markers into their respective squares. The size of a square in the grid changes at different zoom levels.
If more than one state response took place in the exact same location, you can click on the individual marker, and use the arrows and numbers at the bottom of the pop up box to explore the many state responses mapped in this location.
The number indicated on the cluster is the number of individual state response grouped within the cluster.

|
Offensive
|
Defensive
|
Preventive
|
|
State response that aims at confronting and tackling a security threat.
|
State response initiated in reaction to a security incident.
|
State response initiated in order to prevent a potential security threat from occurring.
|
|
Armed military operations
|
Arrests
|
Dismantlement of explosives
|
|
State responses involving the use of heavy artillery and weaponry.
|
Apprehension and detention of individuals.
|
Disassemblement and neutralisation of explosive devices such as landmines, bombs, shells, etc.
|
|
Investigation
|
Raids
|
Restrictions on individual freedoms
|
|
The process of investigating security incidents and/or suspects.
|
Short operations during which security apparatuses storm a place on suspicion of illicit activities or suspects.
|
Limitations of the rights of thoughts, conscience, and opinion.
|
|
Restrictions on digital rights
|
Restrictions on mobility (inc. curfews)
|
Security deployments
|
|
Limitations of the right to access, use, or publish digital medias.
|
Limitations of the right to move freely.
|
Security apparatuses deployment in order to implement an out of the ordinary security measure.
|
|
State of emergency
|
||
|
Government suspension of normal constitutional procedures in situation of national danger.
|

